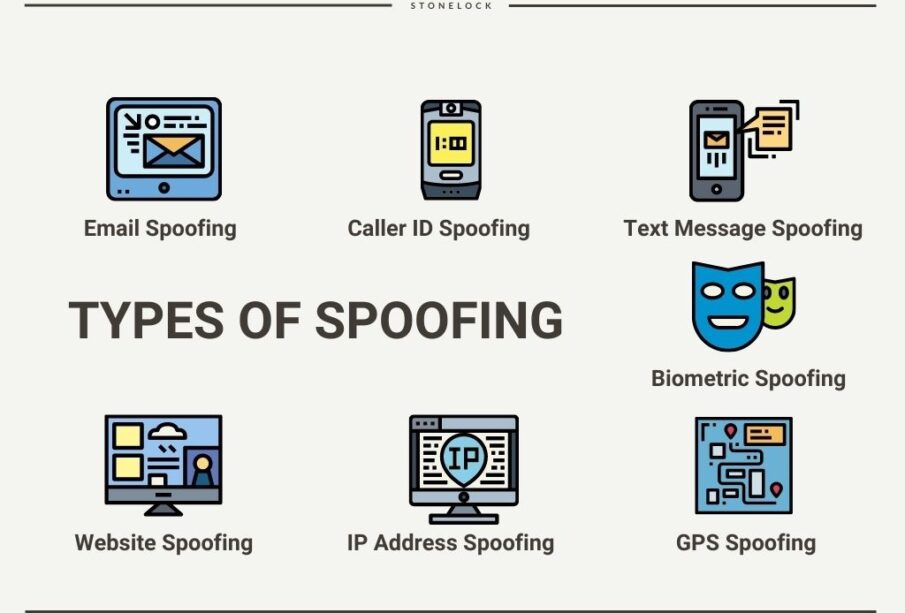
The World’s Most Unusual Spoofing Attack Example
As different ISPs start to put caps on how a lot of information you possibly can download, it turns into even more vital to manage your community. For radio-based mostly attacks, companies can position their antennas so that they’re less doubtless to choose up floor-based alerts and to position them where they can’t be seen by the general public. Relying upon the safety requirements, we will move the threshold worth left or proper, giving an advantage to FAR or FRR. Before we describe DHCP spoofing and poisoning techniques, let’s review the essential workings of the DHCP networking protocol. Let’s consider what may happen if an attacker has been to combine attacks – for instance, DHCP starvation and Rogue DHCP – to launch a Man-In-The-Center attack (MITM).
Let’s review the basics of DHCP allocation and evaluate commonplace DHCP Spoofing strategies. The DHCP server responds with a DHCPACK here to acknowledge the Client’s request and affirm the requested IP address. The request consists of data regarding the client, such as the MAC Deal, so the server knows which consumer sent the request. This may occur even when the request is legitimate, but the server’s address pool is depleted, and no addresses can be found. The client sends a DHCPDISCOVER request by broadcast. A shopper already accustomed to the DHCP server deal can skip a few steps and ship a DHCPREQUEST by unicast directly to the server. The client replies with a DHCPREQUEST to affirm the address provided by the server and requests additional details from the server.
The DHCPOFFER presents the shopper with an IP tackle from the DHCP server’s pool of available addresses and sets the vacation spot IP to the offered tackle. DHCP (Dynamic Host Configuration Protocol) is a utility layer network administration protocol that provides a fast, automatic, and imperative device for the distribution and task of IP addresses and TCP/IP configuration info for purchasers in a community. These protocols ensure that email addresses and e-mail content material will not be tampered with. The purpose of electronic mail spoofing is to trick the recipient of a message into revealing valuable data. When the time for the lease is over, the Shopper will send a DHCPRELEASE message to tell the server that the deal can now be re-distributed to a different shopper.